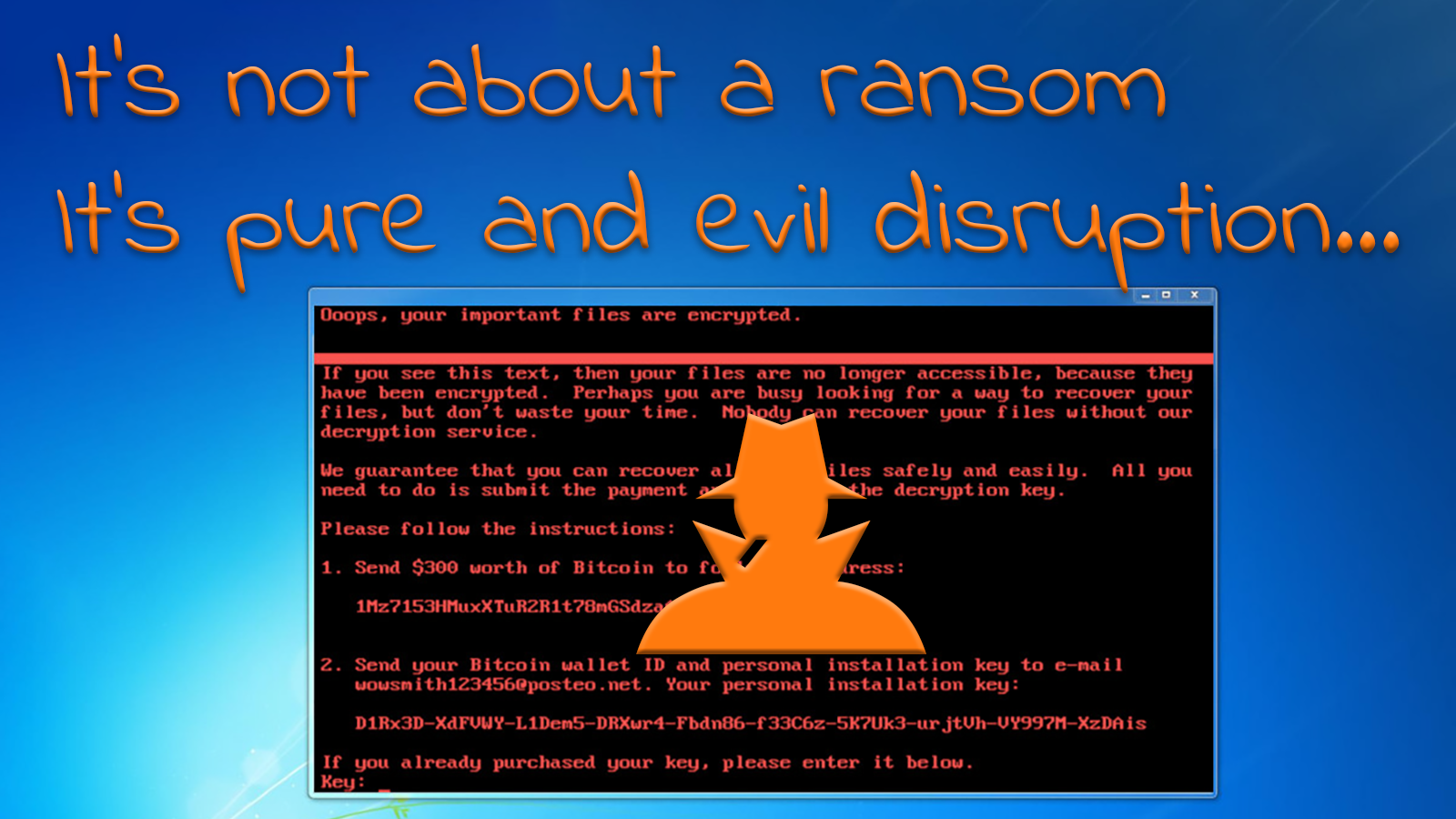
The new generation of ransomware that hit the world last week, is scary, very scary. It’s not about ransom anymore (if it ever was, btw), it’s about pure and evil disruption. Are you prepared for an attack that can disrupt your company? You should be. Any one of us could be next.
CONTENTS: Evil disruption | The 180° switch | Why is this important? | Updates
When the first articles about ransomware appeared, I guess it was late 2014 or early 2015, I immediately saw its potential. It was software with a perfect ‘business model’: encrypt the personal files and ask a ‘reasonable’ amount of ransom for the decryption key, an amount that is lower than the cost to get an IT guy in to fix everything. And do this with many, many people. Over the past two years, there have been a number of attacks, but it wasn’t until earlier this year that they made the headline news.
The first to make the headline news was WannaCry, only six weeks ago. And last week there was Petya (or NotPetya, depending on the sources). The examples of companies that were hit and the economic danger they suffered, are scary. Really and utterly scary. The best known are:
- Moller-Maersk, active in transportation and the world’s largest container line, had to close down multiple container terminals (APM Terminals), including those in the Port of New York and New Jersey, and Rotterdam (Netherlands).
- Mondelez, a global snacks company including the Milka brand, seemed to have had a global IT outage.
- TNT Express (a subsidiary of FedEx), also transportation, had to ground all its planes in the Belgian distribution center.
- WPP, an advertising and marketing company, had to shut down after an attack and it took a few days before full recovery (more info).
Evil disruption
What is even more terrifying, is the analysis of a growing number of experts: it was not about ransom, it was about pure and evil disruption (Techcrunch, CNET). From a ransomware point of view, the execution of Petya was bad: the email address where you had to send the payment proof, was deactivated. Meaning: even if you did pay the ransom, you couldn’t reach the attackers, you couldn’t get the decryption key… Which brings experts to the conclusion that the ransomware was only a ‘wrapper’, not the real reason.
And then we are coming into uncharted territory: who and why? If the attack was intended to disrupt, who wrote it? And why? Leading us to the following question: what can we expect next?
The 180° switch
There is one really important factor in this story: only older systems (e.g. Windows XP) and systems that were not up to date were vulnerable to the attack. And that is the 180° switch that corporate IT needs to make. And needs to make fast.
In the old days, corporate IT always waited quite long before moving to a newer version of the operation system. Even now still about 5% of all Windows systems run Windows XP (it sounds a bit like a joke, but the brand new war ship HMS Queen Elizabeth runs Windows XP…), Windows 7 has a nearly 50% market share…
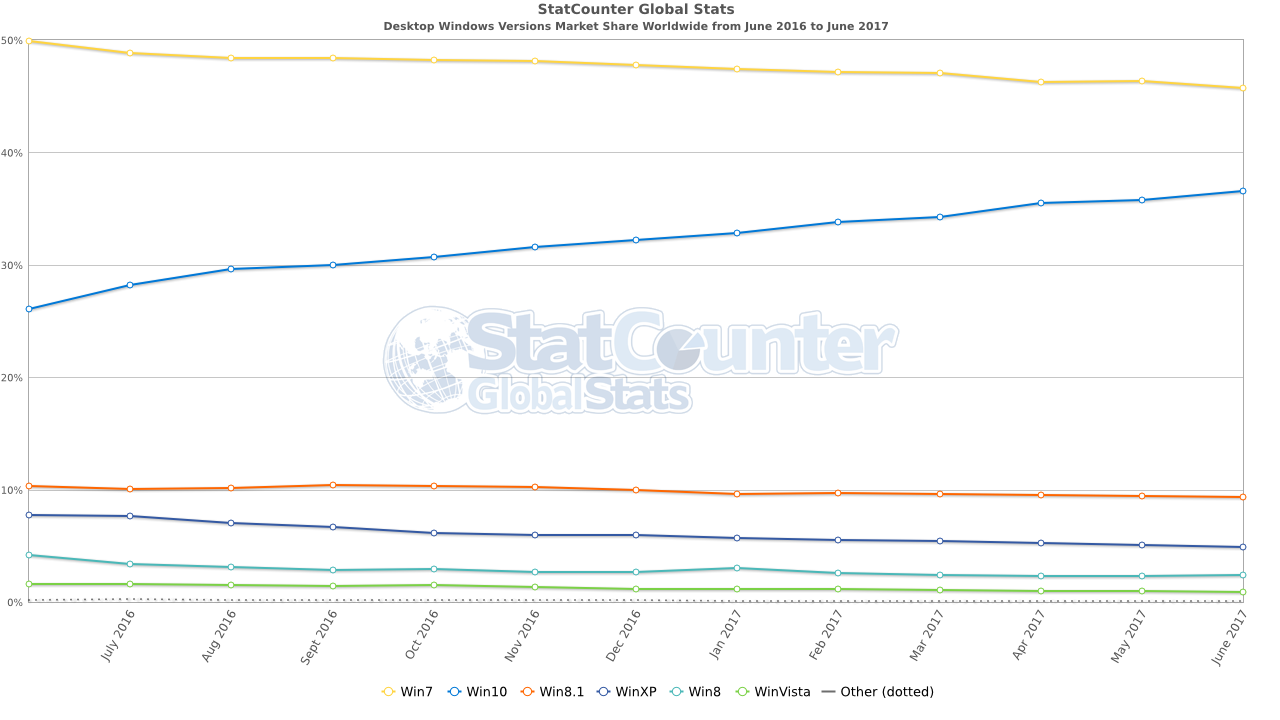
You could argue that it made sense in the old days for corporate IT to wait to upgrade: stability would be better, all bugs were removed through a series of updates. And they had more time to test compatibility with all kinds of (often inhouse built) systems.
But times have changed. At this moment, both Microsoft and Apple share beta versions of the next OS-version with a large number of users, to get the bugs (or at least most of them) out before the official release. E.g. Microsoft has its ‘insider program’, with even a fast and a slow ring (depending on how ‘unfinished’ the version may be for you). The result is that the newest version has been tested much better than, let’s say, a decade ago.
And it’s there that corporate IT could – and should – play a role: be part of those beta-programs, of the ‘insider ring’ in the case of Windows. That way they can already test new versions before they are released and make sure that the incompatibilities and bugs they find, will be fixed in the final version. And then they can upgrade much faster, making them less vulnerable for the devastating attacks we are seeing now.
BTW: it’s not only about Windows, also Mac OS has been attacked, even Linux is not free of those kinds of troubles.
Why is this important?
Don’t think it won’t happen to you. Most of the examples you see in the press are large companies, but small companies are hit as well. And as I already mentioned in an earlier article: 6 out of 10 small businesses that get hit by a ransomware attack, go out of business within the next 6 months… That’s the risk you take if you don’t have proper IT procedures in place, including backup plans (yes, multiple please). Years, even decades of hard work can be destroyed by just opening one mail attachment that looks credible but is infected by the nastiest piece of software that we know at this moment. Be prepared!
PS: Microsoft has analyzed the Petya threat and published their conclusions here. And the main conclusion: Windows 10 is protected against this kind of attacks.
UPDATE 06/07/2017: to put a number of the cost of such an attack, Reckit Benckiser (Dettol, Nurofen, Air Wick, Durex…) announced that it may have lost 100 million GBP in sales due to the Petya ransomware last week…
UPDATE 08/07/2017: Wordfence has published a very technical article how Petya used NGINX and PHP malware in the attack.
UPDATE 12/07/2017: there seems to be a new Android ransomware, which threatens to send all your private info, including browsing history, to all of your contacts…
UPDATE 09/08/2017: today ZDnet published an article which comes to the same conclusion: it’s not about ransome anymore, it’s about evil disruption.
UPDATE 14/08/2017: the UK National Health Service has signed a contract with Microsoft for the support for Windows XP in the future, plus “a centralised, managed and coordinated framework for the detection of malicious cyber activity through its enterprise threat detection software, aiming to reduce the likelihood and impact of security breaches or malware infection across the NHS.” NHS had a similar contract in the past, but ended it in 2015, stating: “We expect most remaining government devices using Windows XP will be able to mitigate any risks, using the CESG guidance.” Which was not the case, as was shown in the WannaCry attack.
UPDATE 16/08/2017: Maersk has given an indication of the cost of the WannaCry attack: 200 to 300 million US $ revenu lost…
UPDATE 22/09/2017: also FedEx / TNT Express has given an estimation of the cost involved with the NotPetya cyber attack: 300 million US $… And the British GCHQ issued a warning that we need to rethink cyber security. Otherwise we can expect cyber attacks that are much worse than WannaCry and others…
UPDATE 30/03/2018: here is a good overview of ransomware and – more importantly – what you can do about it, with screenshots of settings of all kinds of operating systems. A recommended resource!
UPDATE 24/09/2020: here is a recent statistics about ransomware attacks


Be the first to comment