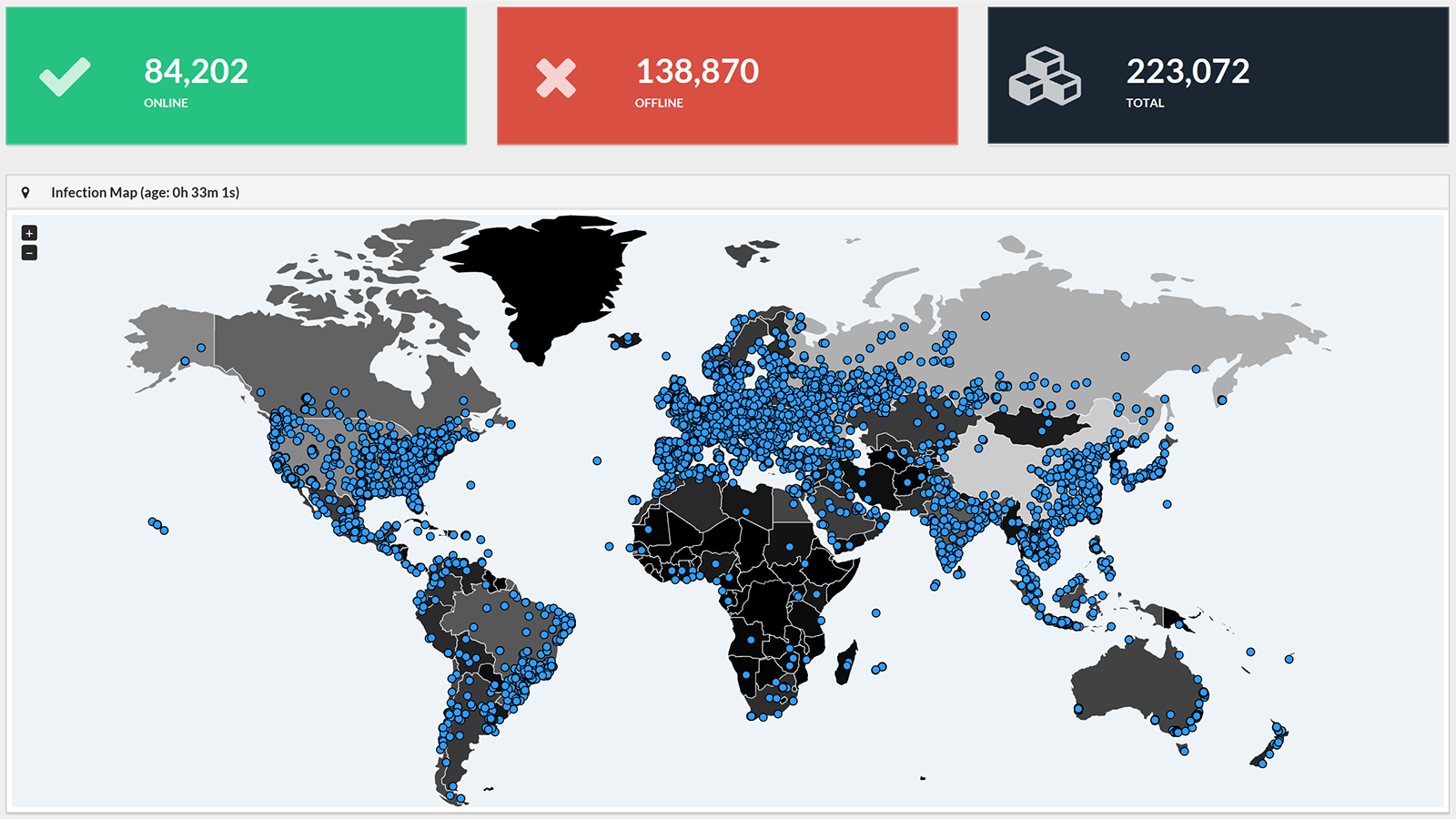
About five months ago, I published a blog post titled “Your resolution for 2017: protecting your company against ransomware”. Unfortunately yesterday the nightmare came true: a massive cyberattack affecting over 100 000 computers, and counting, in at least 99 countries. And this within the first 24 hours. In the UK, at least 39 hospitals were affected, having a significant impact.
CONTENTS: Ransomware: a recap | What to do? | Why is this important? | Updates
Ransomware: a recap
Just in case you are not familiar with ransomware, a short recap: it is a nasty type of ‘computer virus’, one with a perfect business model. When it infects your system, it will start encrypting ALL your files… And you get a warning, telling you that you can get the decryption key if you pay a ransom (hence the name ransomware). This usually is a small amount of money, payable in bitcoins. Although the amount of money is rather small (usually less than 1000 US $), the total turnover of ransomware in 2016 probably exceeded 1 billion US $…
What is ‘interesting’ about ransomware is that over time, they started targeting specific groups: hospitals and more recently SME’s. The first group has a significant amount of computers in their network, raising the chance that somebody will open a malicious document or click on a bad link, and in that network there is a huge amount of confidential and valuable information. The second group usually is less IT minded, with no stringent security measures. When affected, the SME’s are much more willing to pay that small ransom.
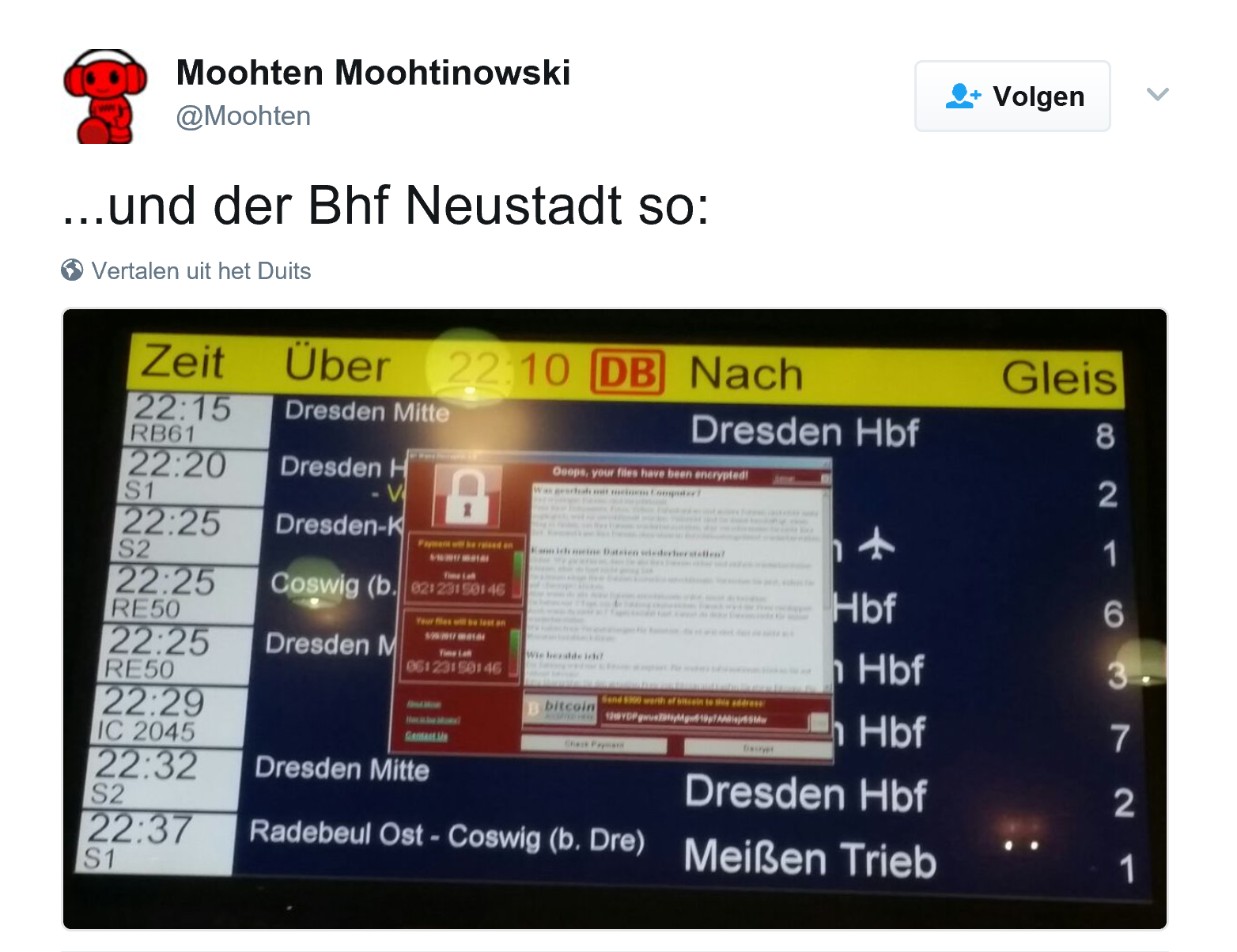
Email messages containing malicious documents are looking very credible: a friend of mine got one which seemed to be from one of his suppliers, claiming that they had attempted to deliver a package the day before and asked to reschedule it via the enclosed Word document. Although he has a good knowledge of IT and security, he ‘missed’ this threat and forwarded it to his secretary, who opened the Word document… and the ransomware started encrypting all her files. Fortunately he immediately disconnected her computer from the network and they had a recent backup, so they were up and running in a few hours.
What to do?
The ransomware that is spreading like hell at this very moment, named WannaCrypt0r or WannaCry, makes use of a known and patched bug in Windows. A patch for the bug was released on the 14th of March. So all systems infected were not up to date! And that’s the first thing to do: keep your systems up to date! I know many larger corporations are not that keen on having the latest software, due to the fear of bugs. But times have changed: new software is now thoroughly tested by large numbers of beta users, making it already very reliable once it is officially released. And second: the bad guys also evolved and keep up with the lists of known and patched bugs, to exploit them.

Next to being up-to-date, it is recommended to have a good security software. Microsoft has already updated the default Windows Defender with the ‘signature’ to detect WannaCrypt. There are also other security software tools that can scan and detect ransomware, I e.g. use MalwareBytes for this purpose.
And make sure you make a backup on a regular basis and make sure that the backup is NOT connected to your network… otherwise ransomware might also encrypt your backup files, rendering them useless.
Why is this important?
After having seen the massive impact during the first 24 hours of this one piece of ransomware, I guess you know why this is important… And in case you are still wondering if this could affect you, read the updates on my original blog post. It contains dozens of examples of new and improved attacks by ransomware.
UPDATE and CORRECTION 14/05/2017: WannaCry has been spreading significantly. The total number of infected IP addresses has grown to over 220 000 in at least 150 countries around the world. In the introduction I incorrectly stated ‘computers’ instead of ‘IP addresses’: multiple computers can be behind one IP address, e.g. in a company network. So the total number of infected computers will be significantly higher.
UPDATE 22/05/2017: a new article by CNET contains a terrifying fact, 6 out of 10 small businesses who get hit by ransomware are out of business within 6 months…
UPDATE 22/06/2017: over the last month numerous infections have been reported. To show the scope and magnitude, here are two from yesterday. Honda had to shut down a production plant earlier this week, due to a WannaCry infection. You don’t want to know the cost of that… And in Victoria Australia, speed cameras were affected too… The Australian Governement has published an interesting document: the Essential Eight Explained. Which provides 8 essential, but easy steps to prevent infection and limit damage.
UPDATE 28/06/2017: just over a month after the WannaCry attack, a new, even more severe cyber attack happened: Petya. The number of examples of companies hit is growing, with a huge economic impact. Some companies had to shut down their entire operations: a large containerterminal in the port of Rotterdam (operated by Maersk), TNT/Fedex in Belgium. The list goes on and on. Here are a number of articles with more information: ZDNet, Techcrunch, WordFence.
UPDATE 29/06/2017: more and more analists are concluding that Petya was not a real ransomware attack, but a cyber attack masked as ransomware. One of the elements to come to that conclusion was the fact that the email address shown in the ransom message, was discontinued. Some even say Petya was a rehearsal for a much bigger attack to come…
UPDATE 30/03/2018: here is a good overview of ransomware and – more importantly – what you can do about it, with screenshots of settings of all kinds of operating systems. A recommended resource!
UPDATE 24/09/2020: here is a recent statistics about ransomware attacks


Be the first to comment